From Jody Jankovsky, Founder and CEO of Black Line IT
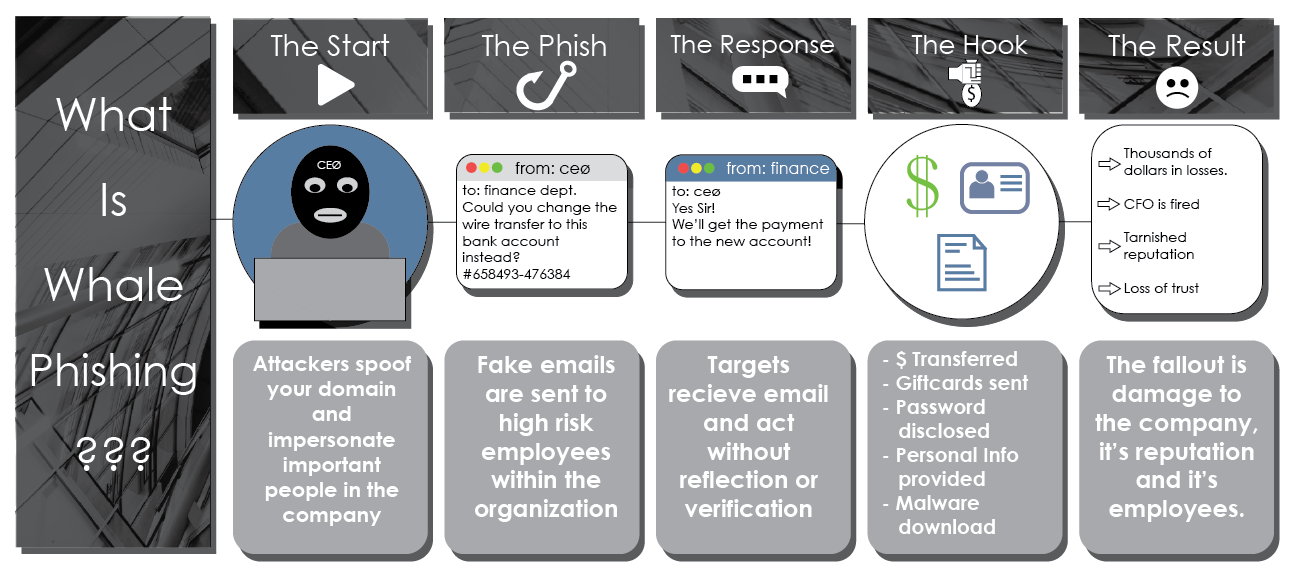
You may have heard of email phishing, but whale phishing takes this crime to a new level - it’s about using technology to catch the big one! Whale phishing is an email scheme where the perpetrator pretends to be someone you trust – and often someone in authority, like your CEO.
Whale phishing falls under the dangerous category of social engineering, which is best described as the use of deception to manipulate individuals into divulging confidential or personal information that may be used for fraudulent purposes. Being victimized by social engineering is the digital equivalent of being conned.
What to Look For
Whale spotting can be tricky, but it can be easier if you keep an eye out for the warning signs.
The sender will impersonate someone you know, such as a family member, friend, superior/co-worker, or even someone from your past. They may also impersonate an entity rather than a specific individual, like the government, your financial institution, or a trusted brand you normally engage with.
Not only do whale phishing emails look like they come from a trusted source, but the content is often believable as well. So how does one spot a whale?
- Financial – if the sender is asking for a financial transaction, dig deeper before taking any action
- Reciprocity or “quid pro quo” – the perpetrator asks for a favor or offers one favor for another
- Authority or Trust – the sender appears to be an authority figure, friend, colleague, or family member, but the content of the email is not a typical conversation with this person
- Commitment/Consistency – the perpetrator is counting on you to follow through because they committed to something in writing
- Social Proof – like technological peer pressure – using the belief if others are doing it, you likely will, too
- Liking – human nature is to be persuaded by those we like, and compliments are a great way to urge someone to do something
- Scarcity/Urgency – creating a feeling of scarcity generates feelings of urgency
- Compassion – people like helping others, and whale phishers use compassion as bait
How Do They Find Your Info?
These perpetrators are tricky, and they find weaknesses and hold on tight. They can find your email address and other information on you through “scraping” social media, your business website, or even public records. (Scraping is an automated process used to extract data in order to gain insights into people and businesses.) They may even gain information by simply calling you and having a conversation, texting, or sending other emails before going in for the big one. There has even been a case documented by the perpetrator hooking a virus to free USB drives they handed out at an event!
So Now What?
Take steps to help keep your business off the hook. Ask your IT department to perform the following:
- Validate no email addresses for your business have been compromised.
- Implement spam filters. If your business already uses spam filters, ask your IT department to evaluate if those filters need adjusting for optimization.
If your business needs resources to prevent or recover from a whale phishing attack, Black Line IT can help - we can assess your security levels to ward off this kind of attack, provide Security Essentials training to your team, and implement the right products and services to keep you protected.
If you already work with Black Line IT, reach out to your Account Owner to learn more. Otherwise, begin a chat/contact us at blacklineit.com/contact (M-F, 8-5 central) or call us at 630.388.1700.
Where do you want to go? Black Line IT will help get you there. We’re ready for your mission.
